Cybersecurity - Misconfigs
Cloud Security: Top 10 Misconfigurations to Avoid
 Quest Lab Team
Quest Lab Team
According to recent studies by Gartner, through 2025, 99% of cloud security failures will be the customer's fault, with misconfigurations leading the way as the primary cause of data breaches and security incidents.
Cloud misconfigurations are essentially incorrect or sub-optimal settings in your cloud environment that can leave your infrastructure vulnerable to attacks or data leaks. These seemingly minor oversights can have major consequences, from data breaches to compliance violations, resulting in significant financial and reputational damage.
"The average cost of a data breach caused by cloud misconfiguration reached $4.41 million in 2023, highlighting the critical importance of proper cloud security implementation."
In this comprehensive guide, we'll dive deep into the top 10 most dangerous cloud misconfigurations, providing detailed insights into why they occur, their potential impact, and most importantly, how to prevent them. Whether you're a cloud architect, DevOps engineer, or security professional, this article will equip you with the knowledge needed to strengthen your cloud security posture.
1. Insufficient Identity and Access Management (IAM) Controls
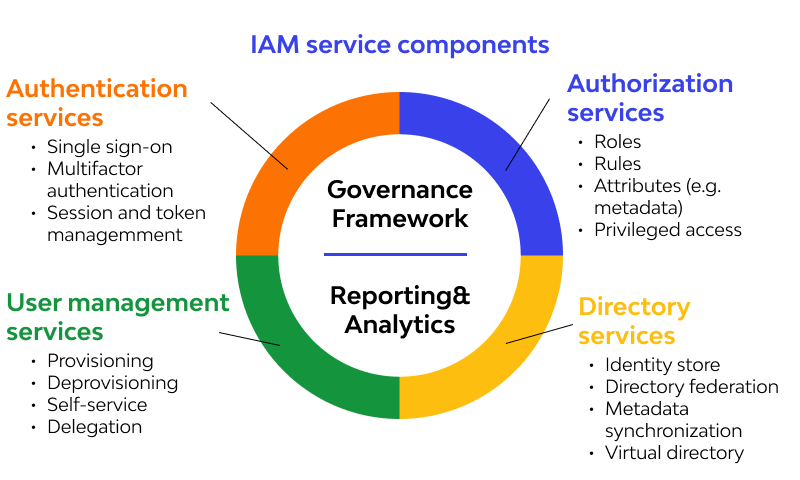
Identity and Access Management (IAM) misconfigurations remain one of the most critical security vulnerabilities in cloud environments. The principle of least privilege (PoLP) is often overlooked, leading to excessive permissions that can be exploited by malicious actors. Organizations frequently create overly permissive IAM roles and policies, granting users and services more access than they need to perform their tasks.
Common IAM Misconfiguration Scenarios
Here are the most frequently observed IAM security mistakes:
- Using root/admin accounts for daily operations
- Failing to implement role-based access control (RBAC)
- Not regularly reviewing and rotating access keys
- Granting broad permissions instead of specific ones
- Neglecting to remove unused IAM users and roles
To properly secure IAM configurations, organizations should implement a comprehensive IAM strategy that includes regular access reviews, automated policy enforcement, and continuous monitoring of permission usage. Implementing just-in-time access and emergency break-glass procedures can significantly reduce the risk surface while maintaining operational efficiency.
2. Exposed Storage Buckets and Containers
Public cloud storage buckets continue to be a significant source of data breaches. Whether it's Amazon S3 buckets, Azure Blob Storage, or Google Cloud Storage, misconfigured access controls can expose sensitive data to the entire internet. The problem often stems from a fundamental misunderstanding of default permissions and the false assumption that cloud storage is secure by default.
- Default Permissions: Understanding that cloud storage services often start with restrictive permissions by default, but can be inadvertently made public through configuration changes.
- Access Controls: Implementing proper bucket policies and access controls to ensure data is only accessible to authorized users and services.
- Encryption Requirements: Enforcing encryption at rest and in transit for all stored data.
- Monitoring and Auditing: Setting up comprehensive logging and monitoring for all storage access attempts.
"A single misconfigured storage bucket can expose millions of sensitive records. In 2023, over 55% of organizations discovered at least one storage bucket with public access enabled."
3. Inadequate Network Security Controls
Network security in the cloud requires a different approach compared to traditional on-premises infrastructure. Many organizations fail to properly segment their networks and implement appropriate security groups and firewall rules. This can lead to unnecessary exposure of services and increased attack surface.
Critical Network Security Measures
Essential network security configurations include:
- Implementing proper network segmentation and VPC design
- Configuring security groups with minimal required access
- Using Network ACLs for additional security layers
- Enabling flow logs for network traffic analysis
- Implementing proper VPN and Direct Connect configurations
4. Misconfigured Security Groups and Firewall Rules
Security groups and firewall rules are your first line of defense in the cloud. Common misconfigurations include allowing unrestricted inbound traffic (0.0.0.0/0) to sensitive ports, failing to implement egress filtering, and not maintaining proper documentation of rule sets. These misconfigurations can lead to unauthorized access and potential data exfiltration.
- Inbound Rules: Restrict access to only necessary ports and source IPs
- Outbound Rules: Implement egress filtering to prevent data exfiltration
- Regular Audits: Conduct periodic reviews of security group rules
- Documentation: Maintain detailed documentation of all security group configurations
5. Insufficient Logging and Monitoring

Many organizations fail to implement comprehensive logging and monitoring solutions in their cloud environments. Without proper visibility into your infrastructure, detecting and responding to security incidents becomes significantly more challenging. This includes failing to enable cloud provider logging services, not implementing centralized log management, and lack of real-time alerting.
Essential Logging and Monitoring Components
A robust logging and monitoring strategy should include:
- Enable comprehensive cloud provider logging (CloudTrail, Azure Monitor, Stack Driver)
- Implement centralized log management and analysis
- Set up real-time alerting for security events
- Regular log review and retention policies
- Integration with Security Information and Event Management (SIEM) systems
6. Encryption and Key Management Issues
Proper encryption and key management are crucial for protecting sensitive data in the cloud. Common misconfigurations include failing to encrypt data at rest and in transit, improper key rotation practices, and inadequate access controls for encryption keys. Organizations often struggle with managing encryption across different cloud services and maintaining compliance with regulatory requirements.
- Data Encryption: Implement encryption for both data at rest and in transit
- Key Management: Use cloud provider key management services (KMS) properly
- Access Controls: Restrict access to encryption keys and regularly rotate them
- Compliance: Ensure encryption methods meet regulatory requirements
7. Vulnerable Container Configurations
Container security misconfigurations have become increasingly common as organizations adopt containerized applications. Issues include running containers with root privileges, using outdated base images, and failing to implement proper container orchestration security controls.
Container Security Best Practices
Essential container security measures include:
- Use minimal base images and keep them updated
- Implement proper container orchestration security
- Scan containers for vulnerabilities
- Implement proper access controls and network policies
- Monitor container runtime security
8. Inadequate Backup and Disaster Recovery
While not traditionally considered a security misconfiguration, inadequate backup and disaster recovery procedures can significantly impact an organization's security posture. This includes failing to regularly test backups, not encrypting backup data, and not maintaining proper retention policies.
- Backup Strategy: Implement comprehensive backup procedures across all critical services
- Testing: Regularly test backup and recovery procedures
- Encryption: Ensure all backup data is properly encrypted
- Retention: Implement and maintain appropriate data retention policies
9. Insecure API Configurations
APIs are often the gateway to your cloud services, and their misconfiguration can lead to significant security vulnerabilities. Common issues include lack of proper authentication, not implementing rate limiting, and exposing sensitive information through API responses.
API Security Essentials
Critical API security configurations include:
- Implement proper authentication and authorization
- Use API gateways for centralized control
- Enable rate limiting and throttling
- Monitor API usage and implement alerting
- Regular security testing of APIs
10. Compliance and Governance Issues
Many organizations struggle with maintaining compliance in their cloud environments. This includes failing to implement required controls, not maintaining proper documentation, and not regularly assessing compliance status. Compliance misconfigurations can lead to regulatory violations and significant penalties.
- Compliance Framework: Implement appropriate compliance frameworks for your industry
- Documentation: Maintain detailed documentation of all compliance-related configurations
- Regular Audits: Conduct periodic compliance assessments
- Automated Compliance: Use cloud provider compliance tools and services
Preventing Cloud Misconfigurations: Best Practices
To effectively prevent cloud misconfigurations, organizations should implement a comprehensive security strategy that includes:
Security Strategy Components
Essential elements of a robust cloud security strategy:
- Implement Infrastructure as Code (IaC) with security checks
- Use cloud security posture management (CSPM) tools
- Regular security assessments and penetration testing
- Comprehensive security training for all team members
- Automated compliance and security monitoring
- Incident response and remediation procedures
Organizations should also consider implementing a Cloud Center of Excellence (CCoE) to maintain security standards and best practices across all cloud deployments. This centralized approach helps ensure consistent security configurations and reduces the risk of misconfigurations.
The stakes have never been higher. The IBM Cost of a Data Breach Report 2023 reveals that organizations with poorly configured cloud environments experienced 27% higher breach costs compared to those with secure configurations. In the first half of 2023 alone, over 33 billion records were exposed due to cloud misconfigurations, marking a 42% increase from the previous year.
Recent Major Incidents
Several high-profile breaches in 2023 highlight the critical nature of cloud security:
- A major healthcare provider exposed 12.5M patient records through a misconfigured S3 bucket
- A Fortune 500 company leaked proprietary code due to incorrect GitHub repository permissions
- A government agency exposed sensitive data through inadequate API security controls
- A financial services provider faced $5M in penalties due to non-compliant cloud configurations
Understanding Cloud Security Posture Management (CSPM)
Before diving into specific misconfigurations, it's crucial to understand the concept of Cloud Security Posture Management (CSPM). According to Gartner, CSPM tools can reduce cloud-based security incidents by 80% through automated identification and remediation of misconfigurations. These tools continuously monitor cloud infrastructure for compliance violations and security risks.
1. IAM Misconfigurations: Deep Dive
Let's examine a real-world example from a 2023 security incident where a misconfigured IAM role at a major cloud service provider led to a significant data breach. The incident occurred when an overly permissive IAM role was assigned to a development environment, allowing lateral movement to production systems.
IAM Security Analysis Tools
Essential tools for IAM security assessment:
- CloudMapper: Analyzes IAM relationships and identifies potential privilege escalation paths
- PMapper: Evaluates IAM permissions and generates visual maps of access patterns
- AWS IAM Access Analyzer: Identifies resources shared with external entities
- CloudTrail Insights: Detects unusual API activity patterns
Advanced Network Security Controls
A 2023 study by the Cloud Security Alliance revealed that 65% of organizations experienced at least one network-related security incident due to misconfiguration. The study highlighted that traditional network security approaches don't translate well to cloud environments, leading to critical vulnerabilities.
Container Security: Advanced Techniques
Container security has become increasingly critical as organizations adopt microservices architectures. According to Red Hat's 2023 State of Container Security report, 94% of organizations experienced container security incidents in the past 12 months, with misconfigurations being the primary cause.
Advanced API Security Configurations
The 2023 OWASP API Security Top 10 report highlights that broken object level authorization remains the most critical API security risk. A study by Salt Security found that 95% of organizations experienced an API security incident in 2023, with misconfiguration being the root cause in 76% of cases.
Encryption and Key Management: Advanced Patterns
A 2023 survey by the Cloud Security Alliance revealed that 82% of organizations had experienced encryption-related incidents, with 43% attributed to key management misconfigurations. The study highlighted that many organizations struggle with key rotation and access control policies.
Advanced Compliance and Governance
The regulatory landscape continues to evolve, with new requirements emerging regularly. The introduction of GDPR 2.0 discussions and enhanced HIPAA requirements for cloud environments has created additional complexity in maintaining compliant configurations.
Conclusion
Cloud security misconfigurations represent a significant risk to organizations of all sizes. By understanding and addressing these top 10 misconfigurations, organizations can significantly improve their security posture and reduce their risk of security incidents. Regular assessment, continuous monitoring, and automated security controls are essential components of a successful cloud security strategy.
"Security is not a one-time implementation but a continuous process of improvement and adaptation. Stay vigilant, stay secure."

Quest Lab Writer Team
This article was made live by Quest Lab Team of writers and expertise in field of searching and exploring
rich technological content on Cybersecurity and its future with its impact on the modern world







