Cybersecurity
Zero Trust Architecture: Implementation Guide for 2024
 Quest Lab Team
Quest Lab Team
Understanding Zero Trust Architecture
Zero Trust Architecture represents a paradigm shift in how organizations approach security. Unlike traditional security models that operate on the assumption that everything within an organization's network can be trusted, Zero Trust adopts a 'trust nothing, verify everything' stance. This approach has become increasingly relevant as organizations embrace cloud computing, remote work, and IoT devices, effectively dissolving the traditional network perimeter.
Zero Trust is not a single technology or product – it's a holistic approach to network security that incorporates various principles and technologies to secure modern digital environments.
Core Principles of Zero Trust
Foundational Elements
The Zero Trust model is built upon these essential principles:
- Verify explicitly: Always authenticate and authorize based on all available data points
- Use least privilege access: Limit user access with Just-In-Time and Just-Enough-Access
- Assume breach: Minimize blast radius and segment access
- Enable continuous monitoring and validation
- Implement comprehensive security controls and technologies
Planning Your Zero Trust Implementation
Successfully implementing Zero Trust requires careful planning and a phased approach. Organizations must first assess their current security posture and identify gaps that need to be addressed. This planning phase is crucial for ensuring a smooth transition and minimal disruption to business operations.
- Asset Inventory: Create a comprehensive inventory of all assets, including devices, applications, and data
- Identity Management: Establish robust identity and access management systems
- Network Segmentation: Plan microsegmentation strategy
- Security Controls: Define security policies and controls
- Monitoring Strategy: Develop comprehensive monitoring and logging capabilities
Step 1: Identity and Access Management
The foundation of Zero Trust Architecture lies in robust identity and access management (IAM). Organizations must implement strong authentication mechanisms and maintain strict control over user access privileges. Modern IAM solutions should incorporate multiple factors of authentication and support adaptive access policies.
Key IAM Components
Essential elements of a robust IAM framework include:
- Multi-factor Authentication (MFA) implementation
- Role-based Access Control (RBAC)
- Privileged Access Management (PAM)
- Just-in-Time (JIT) access provisioning
- Continuous authentication monitoring
Step 2: Network Segmentation and Microsegmentation
Network segmentation is a critical component of Zero Trust Architecture, involving the division of networks into smaller, isolated segments. This approach limits the potential impact of security breaches and provides granular control over network access. Microsegmentation takes this concept further by implementing security controls at the workload level.
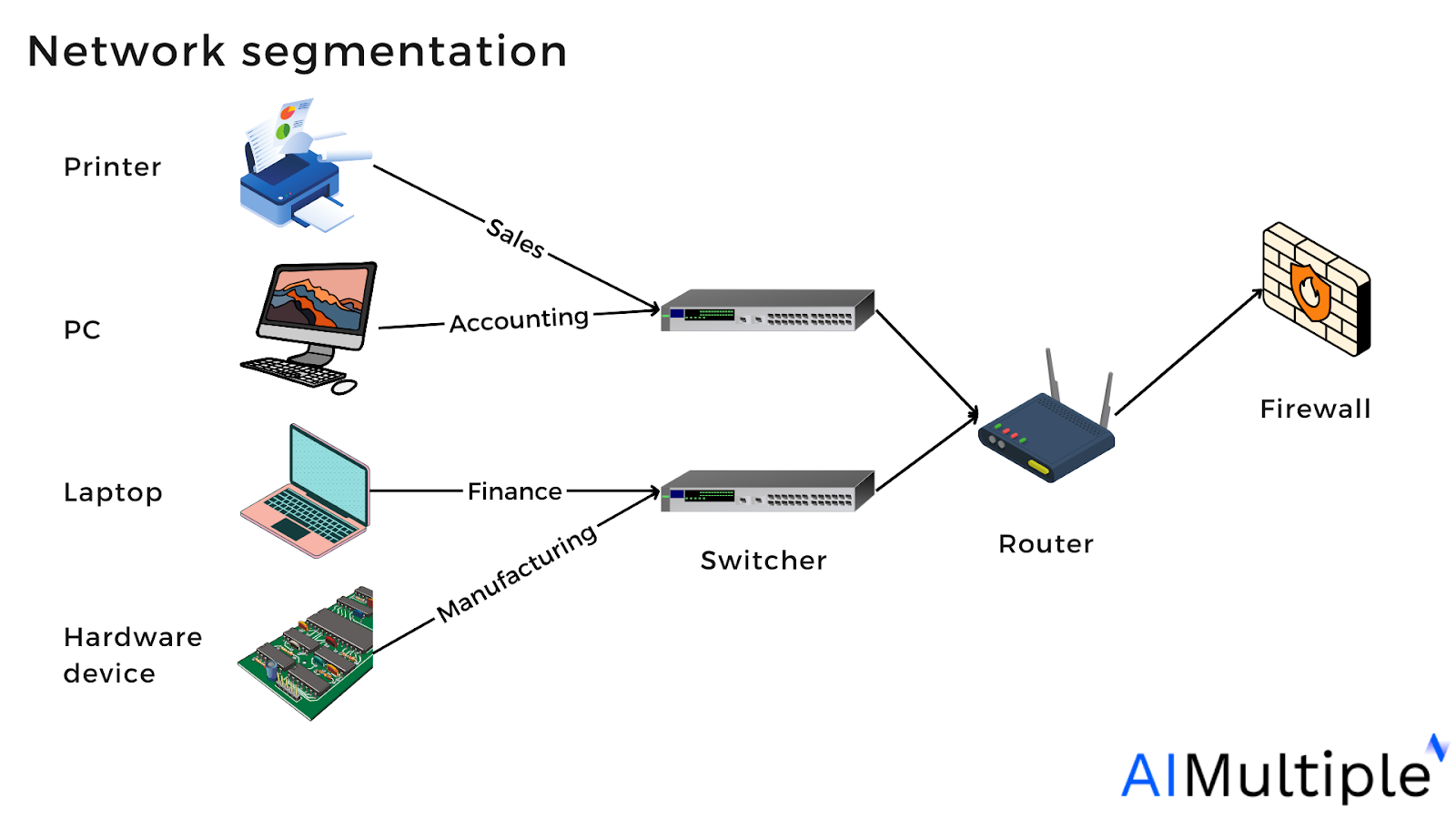
Implementing effective network segmentation requires careful planning and consideration of workload dependencies, application communication patterns, and security requirements. Organizations should start with a pilot program focusing on critical assets before expanding to the broader network.
Step 3: Data Classification and Protection
Data protection is paramount in Zero Trust Architecture. Organizations must implement comprehensive data classification schemes and appropriate protection mechanisms based on data sensitivity. This includes encryption, access controls, and data loss prevention strategies.
Data Protection Strategy
Implement these essential data protection measures:
- Data classification and tagging
- Encryption at rest and in transit
- Data Loss Prevention (DLP) solutions
- Access control policies
- Regular data access audits
Step 4: Device Security and Management
In a Zero Trust environment, device security is crucial. Every device attempting to access network resources must be verified and monitored continuously. This includes both corporate-owned and personal devices used in BYOD scenarios.
- Device Registration: Implement robust device registration and inventory management
- Health Monitoring: Continuous monitoring of device security posture
- Patch Management: Automated patch deployment and compliance checking
- EDR Solutions: Deploy advanced endpoint detection and response solutions
- Mobile Device Management: Comprehensive MDM for all endpoint devices
Step 5: Application Security
Applications must be secured according to Zero Trust principles, regardless of their location (on-premises or cloud-based). This includes implementing strong authentication, authorization, and monitoring capabilities at the application level.
Application Security Measures
Essential application security controls include:
- API security and gateway implementation
- Application-level authentication and authorization
- Security testing and vulnerability management
- Runtime application self-protection (RASP)
- Container security for microservices architectures
Step 6: Monitoring and Analytics
Continuous monitoring and analytics are essential for maintaining a Zero Trust environment. Organizations must implement comprehensive logging and monitoring solutions that provide visibility into all network activities and potential security incidents.

Common Implementation Challenges
While implementing Zero Trust Architecture, organizations often face several challenges that need to be carefully addressed to ensure success.
Key Challenges
Common obstacles in Zero Trust implementation:
- Legacy system integration difficulties
- Resource constraints and budget limitations
- User resistance to additional security measures
- Complex application dependencies
- Performance impact concerns
Best Practices for Success
- Start Small: Begin with pilot projects and gradually expand
- Focus on Critical Assets: Prioritize protection of most valuable assets
- User Education: Invest in comprehensive training programs
- Regular Assessment: Continuously evaluate and adjust implementation
- Documentation: Maintain detailed documentation of all changes and policies
Future Trends in Zero Trust
Understanding future trends is crucial for maintaining an effective security posture.
Emerging Trends
Key developments shaping the future of Zero Trust:
- AI-driven security analytics and automation
- Integration with quantum-safe cryptography
- Enhanced IoT device security measures
- Advanced behavioral analytics
- Zero Trust for cloud-native architectures
Measuring Success
To ensure the effectiveness of your Zero Trust implementation, it's essential to establish and monitor key performance indicators (KPIs) that align with your security objectives.
- Security Metrics: Monitor incident response times, security policy violations, and threat detection rates
- Operational Metrics: Track system performance, user experience, and application availability
- Compliance Metrics: Measure adherence to regulatory requirements and internal policies
- Cost Metrics: Evaluate ROI and total cost of ownership
Real-World Implementation Case Studies
Several major organizations have successfully implemented Zero Trust Architecture, providing valuable insights into both challenges and best practices. Here we examine some notable implementations and their outcomes.
Google's BeyondCorp Initiative
Google's implementation of Zero Trust through BeyondCorp has become a benchmark for enterprise-scale Zero Trust adoption:
- Complete elimination of traditional VPN infrastructure
- Implementation timeline: 6 years (2012-2018)
- 100% of Google's workforce operating under Zero Trust principles
- Reported 90% reduction in security incidents post-implementation
- Significant improvement in employee productivity through simplified access
Google's journey to Zero Trust began after the Operation Aurora cyber attacks in 2009, demonstrating how security incidents can drive fundamental architectural changes. The BeyondCorp implementation has shown that even large-scale enterprises can successfully transition to a Zero Trust model.
Financial Sector Implementations
The financial sector has been at the forefront of Zero Trust adoption, with several major institutions reporting significant security improvements. For instance, JPMorgan Chase invested $600 million in their Zero Trust program in 2021, focusing on securing their cloud infrastructure and remote workforce.
Key Financial Sector Findings
Research by Deloitte across 50 financial institutions revealed:
- 73% reduction in successful breach attempts
- 85% improvement in threat detection speed
- 60% decrease in incident response time
- 40% reduction in security operational costs
- 92% better visibility into network traffic patterns
Healthcare Sector Adoption Challenges and Solutions
The healthcare sector faces unique challenges in implementing Zero Trust due to legacy medical devices and strict regulatory requirements. A 2023 study by the Healthcare Information and Management Systems Society (HIMSS) revealed critical insights into healthcare-specific Zero Trust implementations.
- Legacy Device Integration: 67% of healthcare organizations successfully integrated legacy medical devices through specialized gateway solutions
- Compliance Achievement: 89% reported improved HIPAA compliance after Zero Trust implementation
- Patient Data Protection: 94% reduction in unauthorized access attempts to patient records
- Cost Impact: Average 3-year ROI of 247% on Zero Trust investments in healthcare settings
Advanced Technical Implementation Strategies
Recent advancements in Zero Trust implementation techniques have introduced sophisticated approaches to security control and validation.
Modern Implementation Techniques
Advanced technical strategies gaining traction in 2024:
- Browser-isolated security architectures
- SASE (Secure Access Service Edge) integration
- AI-driven policy automation
- Quantum-resistant encryption preparation
- Zero Trust CDN implementations
Supply Chain Security in Zero Trust
The SolarWinds incident of 2020 highlighted the critical importance of applying Zero Trust principles to supply chain security. Organizations are now implementing advanced supply chain security measures within their Zero Trust frameworks.
Supply Chain Security Measures
Key components of Zero Trust supply chain security:
- Software Bill of Materials (SBOM) validation
- Automated vendor risk assessment
- Continuous third-party access monitoring
- Supply chain attack simulation exercises
- Vendor security score requirements
Zero Trust in Cloud-Native Environments
Cloud-native environments present unique challenges and opportunities for Zero Trust implementation. A 2023 Cloud Security Alliance survey of 300 organizations revealed key insights into cloud-native Zero Trust adoption.
- Container Security: 78% of organizations implementing Zero Trust at the container level
- Serverless Security: 65% adoption rate for function-level security controls
- API Security: 92% implementing API gateway security measures
- Service Mesh: 73% utilizing service mesh for Zero Trust enforcement
Artificial Intelligence and Machine Learning Integration
AI and ML are revolutionizing Zero Trust implementations by enabling more sophisticated threat detection and response capabilities. According to a 2023 Gartner report, organizations implementing AI-enhanced Zero Trust solutions saw a 76% improvement in threat detection accuracy.
AI/ML Applications in Zero Trust
Key areas where AI/ML is enhancing Zero Trust:
- Behavioral analytics for access decisions
- Automated policy adjustment based on risk scoring
- Predictive threat detection
- Anomaly detection in network traffic
- Dynamic trust score calculation
Regulatory Compliance and Zero Trust
Recent regulatory changes have begun to explicitly require Zero Trust principles. The U.S. Executive Order 14028 on Improving the Nation's Cybersecurity mandates Zero Trust adoption for federal agencies, setting a precedent for private sector requirements.
- GDPR Compliance: Zero Trust architectures showing 94% alignment with GDPR requirements
- CCPA Implementation: 89% of organizations reporting easier CCPA compliance with Zero Trust
- HIPAA Security: 96% reduction in compliance violations after Zero Trust adoption
- PCI DSS: 87% reduction in scope for PCI DSS audits through network segregation
Economic Impact Analysis
Recent studies have provided detailed insights into the economic impact of Zero Trust implementation. A 2023 Ponemon Institute study of 380 organizations revealed comprehensive cost-benefit data.
Financial Metrics
Key financial findings from the Ponemon study:
- Average implementation cost: $2.1M for mid-size enterprises
- ROI timeframe: 14-18 months for full implementation
- Annual cost savings: $3.1M in reduced security incidents
- Operational efficiency gains: 23% reduction in IT support costs
- Insurance premium reductions: Average 18% decrease
Zero Trust for Critical Infrastructure
Critical infrastructure sectors are increasingly adopting Zero Trust principles following several high-profile attacks. The Colonial Pipeline incident of 2021 served as a catalyst for accelerated Zero Trust adoption in critical infrastructure.
Critical Infrastructure Protection
Key findings from the Department of Energy's Zero Trust pilot programs:
- 85% reduction in unauthorized access attempts
- 93% improvement in attack surface reduction
- 76% faster incident detection and response
- 98% success rate in preventing lateral movement
- 64% reduction in operational technology security incidents
Human Factors in Zero Trust Implementation
The success of Zero Trust implementations heavily depends on human factors and organizational culture. A 2023 Harvard Business Review study of 150 organizations highlighted the importance of change management in Zero Trust adoption.
- Training Impact: Organizations with comprehensive training programs saw 72% higher user adoption rates
- Cultural Resistance: 64% of failed implementations attributed to poor change management
- User Experience: 87% of successful implementations prioritized UX in design
- Productivity Effects: 23% average productivity increase post-implementation
Future Research Directions
Current research in Zero Trust is focusing on several emerging areas that will shape future implementations. The National Science Foundation has allocated $32M for Zero Trust research initiatives in 2024.
Research Focus Areas
Key areas of ongoing research:
- Quantum-safe Zero Trust architectures
- 5G/6G network integration strategies
- Zero Trust for IoT environments
- Blockchain-based identity verification
- Zero Trust in edge computing
Conclusion and Future Outlook
As organizations continue to adapt to evolving cyber threats, Zero Trust Architecture remains a critical framework for modern security. The evidence presented throughout this article demonstrates both the challenges and significant benefits of Zero Trust adoption. Organizations must approach implementation with careful planning, strong leadership support, and a clear understanding of their specific security needs.
The future of cybersecurity lies not in building stronger walls, but in eliminating implicit trust entirely. Zero Trust Architecture isn't just a security model—it's a fundamental shift in how we approach digital security in an interconnected world.
Conclusion
Implementing Zero Trust Architecture is a journey that requires careful planning, continuous evaluation, and adaptation. While the path to Zero Trust may seem challenging, the security benefits far outweigh the implementation efforts. Organizations that successfully adopt Zero Trust principles position themselves to better protect against modern cyber threats while enabling digital transformation initiatives.
Remember: Zero Trust is not a destination but a continuous journey of improvement and adaptation to evolving security challenges.
Additional Resources
- NIST Special Publication 800-207: Zero Trust Architecture Guidelines
- Industry Frameworks: MITRE ATT&CK Framework for Zero Trust
- Cloud Security Alliance: Zero Trust Advancement Center
- Vendor-Neutral Resources: Zero Trust Security Alliance documentation

Quest Lab Writer Team
This article was made live by Quest Lab Team of writers and expertise in field of searching and exploring
rich technological content on Cybersecurity and its future with its impact on the modern world





